India’s second-largest cryptocurrency exchange CoinDCX fell victim to one of the most sophisticated crypto heists of 2025 in India, losing $44 million in a meticulously planned attack which matches any digital crime thriller.
The Attack
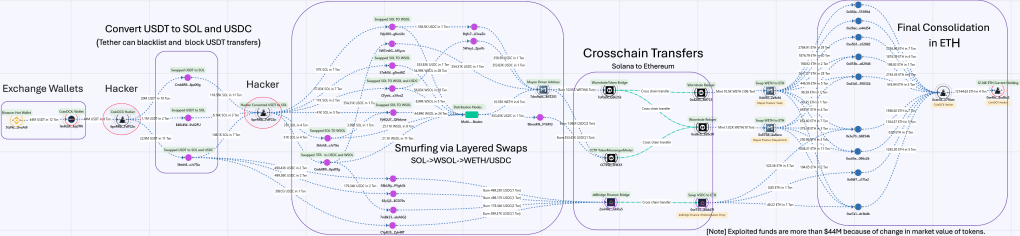
On July 19, 2025, hackers breached CoinDCX’s internal operational wallet that was managing liquidity operations. The breach targeted their backend systems with technical precision. What followed wasn’t just a simple theft – it was a complex web of cryptocurrency laundering that showcased the most advanced evasion techniques we have recently seen.
The attacked wallet (the liquidity wallet), was funded by the Binance hot wallet. CoinDCX, post the attack, published a incident report and proactively opened up a bounty program to recover the lost funds and began the investigations.
Stablecoin Conversion for Blacklist Evasion
Once inside CoinDCX’s systems, the hackers immediately converted the stolen USDT (Tether) tokens into SOL (Solana’s native cryptocurrency). This wasn’t random – it was a calculated move to avoid the “blacklisting” that can freeze USDT tokens in their tracks. In past, around $1.4B has been frozen by Tether, following the illicit transactions trails Source.
USDT blacklisting has become a major threat to crypto criminals. Tether can freeze suspicious addresses, but there’s a critical flaw: the process takes time. Recent reports show that delays in Tether’s blacklisting system allowed over $78 million in ill freezing could take effect. Source
The Art of Smurfing and Token Swaps
The hackers then employed a technique called “smurfing” – breaking large sums into smaller, less suspicious amounts. It’s one of the digital equivalent of old-school money laundering through multiple shell companies. Instead of moving $44 million in one transaction, they distributed funds across multiple wallet layers, making detection very difficult.
This layering technique, commonly known as “hops” in the crypto community, involves transferring funds through multiple intermediary wallets—typically between three to five hops in this case. Each hop complicates the transaction trail and makes it harder for authorities to trace the money’s origin. The native SOL was swapped to WSOL (Wrapped SOL) and then swapped again to WETH (Wrapped Ether Token Solana) and USDC(USD Circle Token on Solana) for further cross chain transfers.
SOL-> WSOL-> WETH/USDC
Cross-Chain Movements
The real sophistication came in the cross-chain movement. The hackers had WETH (Wrapped Ethereum) and USDC, before bridging these assets to the Ethereum blockchain.
The funds reached :
– the deBridge Finance,
– Wormhole Token Bridge through Mayan Finance.
The Wormhole internally used protocols such as CCTP Token Messenger along with additional cross-chain solutions to continue moving and processing the assets.
The Final Consolidation
Despite all the swaps, the hackers ultimately consolidated their stolen funds into a single Ethereum wallet address: 0xef0c5b9e0e9643937d75c229648158584a8cd8d2, as on 28th July 2025 this address holds 12,144.63 ETH,which was acquired through 9 different addresses.
Few major address are:
- CoinDCX’s compromised address Solana-Ge8dzF234QHZKFh7TYyZqdipn3BoHyZfoyz9fxEqdTRi
- Binance hot wallet- Solana-5tzFkiKscXHK5ZXCGbXZxdw7gTjjD1mBwuoFbhUvuAi9
- Attacker’s address -Solana-6peRRbTz28xofaJPJzEkxnpcpR5xhYsQcmJHQFdP22n
- Attackers consolidation Address on Ethereum: 0xef0c5b9e0e9643937d75c229648158584a8cd8d2


Leave a reply to Shahbaz Ahmad Cancel reply